-
-
Notifications
You must be signed in to change notification settings - Fork 3.4k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Let's Encrypt intermediate not accepted by Chrome and IE8 on Windows XP #1660
Comments
|
It wouldn't be the certificate that is not compatible but the implementation of it, as the procurer of the certificate it would your job to ensure its works for your user base, for XP users, they should upgrade to 7-10 or use a proper OS, such as Fedora or Ubuntu. If they insist on using crap, you will need an IP per certificate, letsencrypt have chosen to use SNI (good for them), although SNI should work on Chrome6 in XP.. what service pack are you running? |
This is not an SNI issue, as you can see from the screenshots. I am being provided with the correct The screenshots are from my Windows XP virtual machine, that has SP3 and all available Windows updates applied. It's running Chrome version 47.0.2526.73 m. |
|
If anyone wants to reproduce this issue, Windows XP virtual machines are available from Microsoft: https://dev.windows.com/en-us/microsoft-edge/tools/vms/linux/ aaronmehar is right that you can't test IE8 on |
|
I found that the "Extended Error Information" gives some additional detail... It seems that it's getting confused by the Notice how it thinks RFC 5280 about x.509 Name Constraints: https://tools.ietf.org/html/rfc5280#section-4.2.1.10 |
|
I've confirmed this using the Windows XP VM from https://dev.windows.com/en-us/microsoft-edge/tools/vms/linux/. I'll update our FAQ, and we can look at how to fix the issue longer-term. |
|
@jsha Thanks. Should I create a new issue to fix WinXP compatibility, or rename/edit this one? |
|
Any fix is going to be an administrative/signing issue for Let's Encrypt, not something specific to either the client or the server. So I'm closing out this issue. The problem is documented on the community forums now, and we'll track any possible fixes internally. Thanks so much for digging into it! |
|
thanks @jsha for the clarification.. maybe this can make it into official manual too at https://letsencrypt.readthedocs.org/en/latest/intro.html ? |
That's not saying much. Will you be working to create a new intermediate certificate to enable Windows XP compatibility, or is this just a polite "wontfix"? |
|
@intgr: Sorry I can't commit more! This is a polite "very busy with post-launch at the moment, need get together a quorum of colleagues to discuss the issue in detail." :-) |
|
For anybody with this issue it is possible to work round with Apache and mod_rewrite using the following code
Basically pop this in your :80 .conf and Windows XP users will not be redirected to https but everything else will. You can add other user agents as required. |
|
+1 |
|
(Probably) the same problem is with Android 2.3. Certificate is loaded correctly (no SNI or protocol problem) but is refused because of "domain mismatch". Forum topic: https://community.letsencrypt.org/t/san-domain-name-mismatch-android-2-windows-xp/4060 |
|
I suspect that problem is not in intermediate certificate but actualy in the issued end certificate - in a X509v3 Certificate Policies field that windows xp certification managment tool see as hex gibberish (and in case of all other certificates on the internet it is not so). Owner of the project: please test by issuing end certificate without X509v3 Certificate Policies field or set it to something simpler or at least move it higher in the structure so its not directly below X509v3 Subject Alternative Name as its seem to interfere with it |
There are no problems with certificate on android 2.3.6 stock browser as I tested. |
|
Opera has the same problem as Chrome. |
|
I think it would be very helpful if the generated apache configs would take these into account and WXP wouldn't redirect to https. |
|
knyttl this configuration is for apache. Have you some idea how do that on haproxy? |
|
In the end it doesn't help as the :443 won't redirect on invalid certificate. Anyone who bumps into https:// will get the error. Now it seems to me that these certificates are completely useless. |
|
It cannot be solved with redirects. It doesn't work for links to https (from Google for example) and it is huge security risk. |
|
@Soukiii: Yes you are right, my mistage. This means there is no way to overcome this issue for WXP users. I can't imagine any website which could settle down for only non-wxp users. |
|
@knyttl Well if you want to be PCIDSS compliant you can no longer use TLSv1 which affects a lot more that XP users, it goes to IE10 on Windows 7. So while this bug is annoying lots of sites will have to exclude IE and Chrome on XP and a whole lot more if they want to take credit card details. |
|
For the folks who want a way to redirect some but not all of their visitors to HTTPS, there's a new ticket about that client functionality: #1942 |
|
Since this ticket is closed, is there anywhere that we can subscribe to follow when WinXP becomes compatible? |
|
With the following Javascript code, the browser tries to load a file over https. If that works, the user gets redirected to https (source: http://stackoverflow.com/a/27896066). This might be useful if you only want to redirect browsers that support your cipher suites. In contrast to above approach (#1660 (comment)), this code also redirects visitors that use Firefox in Windows XP. |
|
@dasa123 That's just wrong. |
|
@Soukiii I know it's not an ellegant solution. I myself just use the following on my webserver: But, the approach might be a viable option if you don't want to think about which browsers support SNI. |
|
No, it's not. Visitor clicks on HTTPS link in Google and gets error page - javascript doesn't even load. Https would be totally pointless if it could be disabled by untrusted certificate. |
Not everybody wants to take the risk of a big bang deployment of https-only website access and thus might set their Google Webmaster Tools and robots.txt up accordingly in order to get http links listed in the search engine results. You can't assume that every webmaster wants their website linked via https.
The code/redirect isn't supposed to run over https anyway:
And https-only access protects you?! To prevent this: HSTS, HPKP, DANE, DNSSEC/TLSA Validator, certificate transparency |
|
The thing is @dasa123 , if you can afford to initiate insecure connection if ssl fails why can't you just do it for everyone else and drop ssl support completely? And if the data going on the line is half critical, how can you afford to compromise users just to have more traffic ? I think security best practice learned us that if you can't serve on a secure connection you should fail the connection with as much bells and whistles. It is in the user best interest not to interact with your site if the connection is not secure. And you are right that https-only is only making one link in the security chain stronger, but I don't see how this is a case for making it weaker. |
|
@yonjah Like I said, big bang deployment is not a solution for everybody. https deployment is always a tightrope walk between security and usability. If Google would follow your argumentation, they would drop RC4 based ssl ciphers. But, they want to support legacy systems and still support insecure ciphers (https://www.ssllabs.com/ssltest/analyze.html?d=www.google.com&hideResults=on). You as a security focused person are often not the sole policy maker. This is especially true if you are responsible for a company website where the company managers, important customers etc. have a say, too.
You can grant website visitors different levels of usage rights, e.g.:
If hardly any website visitor comes without https support, you make the switch to https-only access.
You might not be the sole decission maker. The company might earn their money with the website...
https is flawed by nature. Just because you allow access only over https doesn't mean that the connection can't be "disabled by untrusted certificate" (#1660 (comment)). A recent case: https://security.googleblog.com/2015/03/maintaining-digital-certificate-security.html |
@dasa123 Google are in the process of dumping rc4 - Also there is huge different between using rc4 which will offer a bit less secure connection to small part of your users (users using evergreen browsers without rc4 support are not affected, and even if an rc4 connection is made, a real world attack is hard to implement (best I know is ~50 hours for decrypting a cookie). Compare to your suggestion where XP users by design don't have any security at all, and all a MITM has to do is to drop ssl connections and now any users will not have any secure connection at all.
I think this approach is totally OK if you need to have maximum availability and don't have any other choice. But your JS code (and any other solution that was offered here ) doesn't offer this solution. Any one who wish to implement this kind of solution will have to probably write it specifically for their infrastructure and the little code you have here to detect ssl has little value to none in that context. If we go back to the company that want maximum availability and security for there users, they shouldn't use Letsencrypt until an xp support is available, since there are a lot of CAs out there that support XP this is a no brainer. |
... and they don't make it via big bang deployment which was the main point of this argument. They first announce, wait, test etc.
If there is somebody having the motivation to act as a MITM and attack your website, you will not be protected by https-only either unless in some scenarios where such technologies as HPKP, HSTS, DANE etc. come into play. I didn't deny that the redirect is problematic.
... and that's not what I claim.
Anybody who just applies brainless copy and past should just use the services of professionals, pay their monthly fee and avoid implementing Let's Encrypt on their system.
Even if you use such a CA, there might be other web clients not supporting your chosen webserver https settings or people still might want to redirect if possible. I think it's unrealistic to switch from http to https-only from one day to another. |
|
They fixed the incompatibility (not completely because it currently requires a little tweak — see below): https://community.letsencrypt.org/t/upcoming-intermediate-changes/13106! I renewed my certificate (by the way, I have one cert for multiple domains): Then I changed nginx' parameter ssl_cipher (see https://wiki.mozilla.org/Security/Server_Side_TLS#Recommended_configurations) (the following one doesn't support IE6): Then I tested my websites with Chrome and IE8 on Windows XP SP3 (no warnings, no errors). |
|
Thanks for the input all! I'd encourage you to use the community forum to continue the conversation about how and whether to run a web server that supports both XP and newer operating systems. |
But it would be clever of them to do so as Google ranks HTTPS sites higher. 😃 |
|
win7 Chrome 53 with "This page is insecure (broken HTTPS)." |
|
xiaobailong24, what page? |
|
Let's Encrypt fixed the original problem. Perhaps this is more likely to be SNI, which will still produce errors in Chrome and IE, but not Firefox, on WinXP for VirtualHost's other than the first one. If it's that, it's an XP problem, not a Let's Encrypt one. |
|
I hope, "win7" is not XP :) |
|
@Chupaka Thanks for your reply. My test page is https://www.aigoogle.club |
|
@xiaobailong24 your domain does not match the certificate - it's issued only for aigoogle.club, not for www.aigoogle.club. |
|
@Majkl578 Thank you a lot. That's my mistake. It's OK now! |
|
Chrome 54 on Android has the same problem, and that's not exactly an old platform… oddly, Chrome 55 on desktop works fine instead… |
|
@Lohoris: Most likely you're experiencing a different problem. Chrome 54 on Android usually works fine with Let's Encrypt. Can you post at https://community.letsencrypt.org/ with the name of the site you're having a problem with, and a screenshot of the error? |
|
Ok, I've opened a new issue over there, thanks. https://community.letsencrypt.org/t/invalid-certificate-on-mobile-works-on-desktop/24295 |
|
When testing a website created with certbot on https://www.ssllabs.com/ssltest/analyze.html, I can see a confirmation that it works for Firefox and Chrome on Windows XP but not Internet Explorer: |
|
The LetsEncrypt certificate problem with XP was fixed a long time ago. Your problem is that SNI is not supported in IE (or Chrome, I thought) in XP for https sites, which is nothing to do with LetsEncrypt. |
|
Thanks, so even with the manual configuration, Let's Encrypt will never work with Internet Explorer on Windows XP? |
|
It does work on Windows XP. It just won't work if there are several TLS sites on single IP address. |
|
@baptx Please post about your site (including the full domain name) at https://community.letsencrypt.org/ and hopefully people will be able to help you debug your issue there. Thanks! |
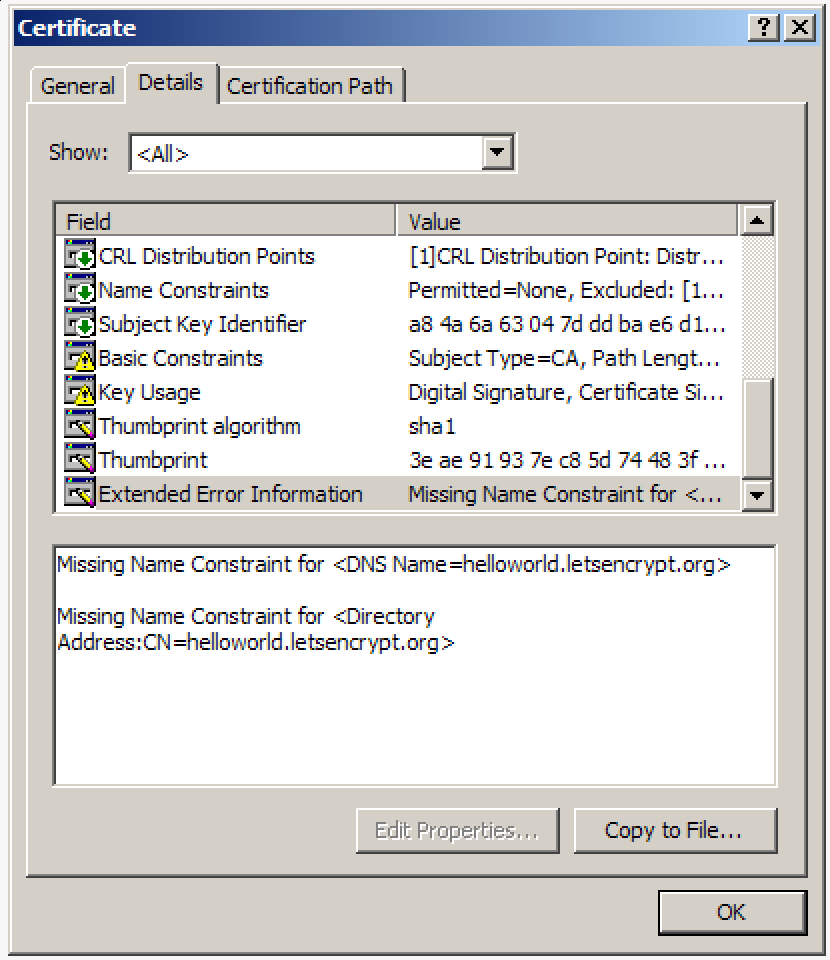
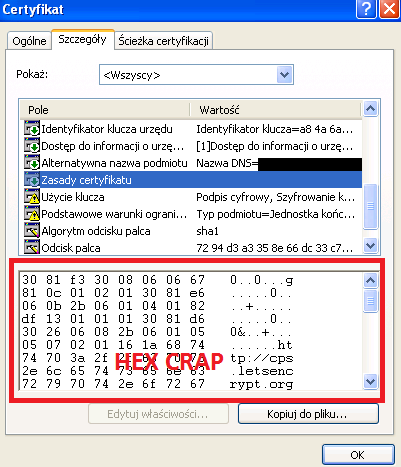
I know and I've heard all the caveats that Windows XP is unsupported, etc etc. But there's still a significant user base left on Windows XP.
If Let's Encrypt certificates are officially known to be broken on Windows XP, that's fine. But there should be a clear official statement of that fact somewhere (e.g. Let's Encrypt FAQ), so everyone who has this issue, knows that they're SoL.
Screenshots of Chrome on Windows XP with certificate details:
The text was updated successfully, but these errors were encountered: