data sovereignty
What is data sovereignty?
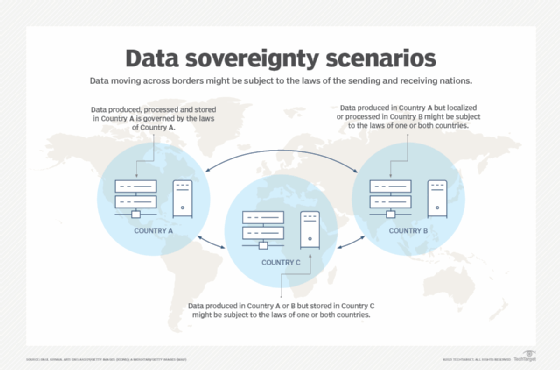
Data sovereignty is the concept that information that has been generated, processed, converted and stored in binary digital form is subject to the laws of the country in which it was generated. It can be stored in the country where it was created, or it can be stored -- but not processed -- in another country, under what is referred to as data residency. If data that is resident in another country is processed in that country, it is referred to as data localization. That data must comply with data sovereignty rules in the nation it's resident in and might also have to comply with the laws of the country it was generated in.
Many situations arise in which data is generated and then transmitted and remotely processed. Organizations operating in multiple countries sometimes establish their own data centers in those countries. Other options include working with a service provider in those countries or a cloud service provider that has experience dealing with data sovereignty issues.
Why is data sovereignty important?
Many organizations -- both public and private sector -- operate in multiple countries. Understanding data sovereignty is key to ensuring data remains secure both in transit and at rest. It also helps organizations stay compliant with all applicable laws and regulations.
Businesses must maintain the confidentiality, integrity and availability of the data they generate, process and hold regardless of its location or processing status. Data sovereignty rules and regulations vary from country to country. Agreements among nations addressing data sovereignty are often complex and involve any parties touching the data in question.
Many data sovereignty requirements relate to the enforcement of data privacy regulations in each country and when data crosses national borders. Another issue is knowing which laws and regulations apply to data that's created in one country but resident and processed in another country.
Key concerns surrounding data sovereignty include data security, cybersecurity, data privacy, protection of sensitive data, protection from data breaches and malware, and access controls so that information is available when needed. Multinational companies must be diligent when it comes to understanding and complying with the data protection laws and regulations of countries in which they operate.
How is data sovereignty determined?
When data is collected in one country and processed in another country, the concept of data sovereignty comes into play. The rules that apply to this situation vary depending on the specific laws and regulations of the countries involved. Generally, data sovereignty implies that the country in which the data is collected holds jurisdiction and authority over that data. In other words, the country where the data is collected can enforce its laws and regulations on how the data is stored, processed and protected.
However, when data is processed in another country, it might also be subject to the laws and regulations of that country. This can potentially create conflicts, especially if the data protection and privacy laws and regulations differ between the two countries.
In such cases, organizations must ensure compliance with the laws and regulations of both countries. They might need to implement measures to protect data, such as entering into data protection agreements, implementing data transfer mechanisms compliant with local regulations and seeking legal advice to navigate potential conflicts.
It's crucial for organizations to be aware of the data sovereignty landscape and understand the legal requirements of the countries involved in their data collection and processing. This includes being knowledgeable about data protection laws, cross-border data transfer restrictions, and appropriate measures to maintain data privacy and security.
Who needs to understand data sovereignty?
Any organization doing business in one or more foreign countries must be aware of data sovereignty laws and regulations in each of the countries in which it operates. Data protection officers (DPOs) are charged with protecting their company's data regardless of location. A DPO ensures a company is in compliance with data sovereignty regulations. Failure to comply with regulations can result in litigation, fines and other costly remedies.
The European Union's General Data Protection Regulation (GDPR) requires that companies that handle the personal data of EU citizens have a DPO on staff. GDPR is an example of how one entity's regulation affects multiple businesses in other countries.

How does data sovereignty work?
Organizations that wish to process and store data in other countries should take the following steps:
- Know applicable laws and regulations. Multinational businesses must identify the data sovereignty laws and regulations that affect on-premises and cloud-based data in other countries.
- Communicate with appropriate bodies. These businesses should let the appropriate agency in each foreign country know their data storage, processing and transfer plans. This involves proposing an agreement that permits them to process and store data -- or other related activity -- in each country.
- Hire local experts. It might be necessary to contact firms with expertise in such regulatory agreements. Any organization working with a public cloud service provider or a multi-cloud setup to support its overseas operations should check that the cloud vendor has agreements in place for data processing, storage and transmission in the designated countries.
Cloud computing data sovereignty challenges
The adoption of cloud computing services as well as advances in data storage, such as object storage, have broken down traditional geopolitical barriers. In response, many countries have established regulations for data governance and transborder data flow by amending laws or launching new legislation that specifies where customer data is to be processed and stored.
Cloud service vendors often have data centers in several countries and agreements in place to accommodate international data sovereignty regulations. It's essential to verify that such agreements are in place and that the vendor has in-house data protection specialists overseeing data issues.
It can be difficult for customers to verify that data exists only at allowed geographical locations in a cloud infrastructure. That's why they must trust that their cloud providers are honest and open about where their servers are hosted and that they adhere to service-level agreements that address sovereignty issues.
Learn more about cloud storage data residency and how to ensure you're in compliance with local laws and regulations.
