-
Notifications
You must be signed in to change notification settings - Fork 9.3k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Implement a layout-blocking property on networkrequests in Blink #2065
Comments
|
weren't we switching to some (future) debugger-protocol-based detection for this? Or was that something else |
|
IIRC, @pavelfeldman was going to do something with blocking resources in the protocol. |
|
Exposing a render-blocking bit in the protocol would solve a lot of problems. |
|
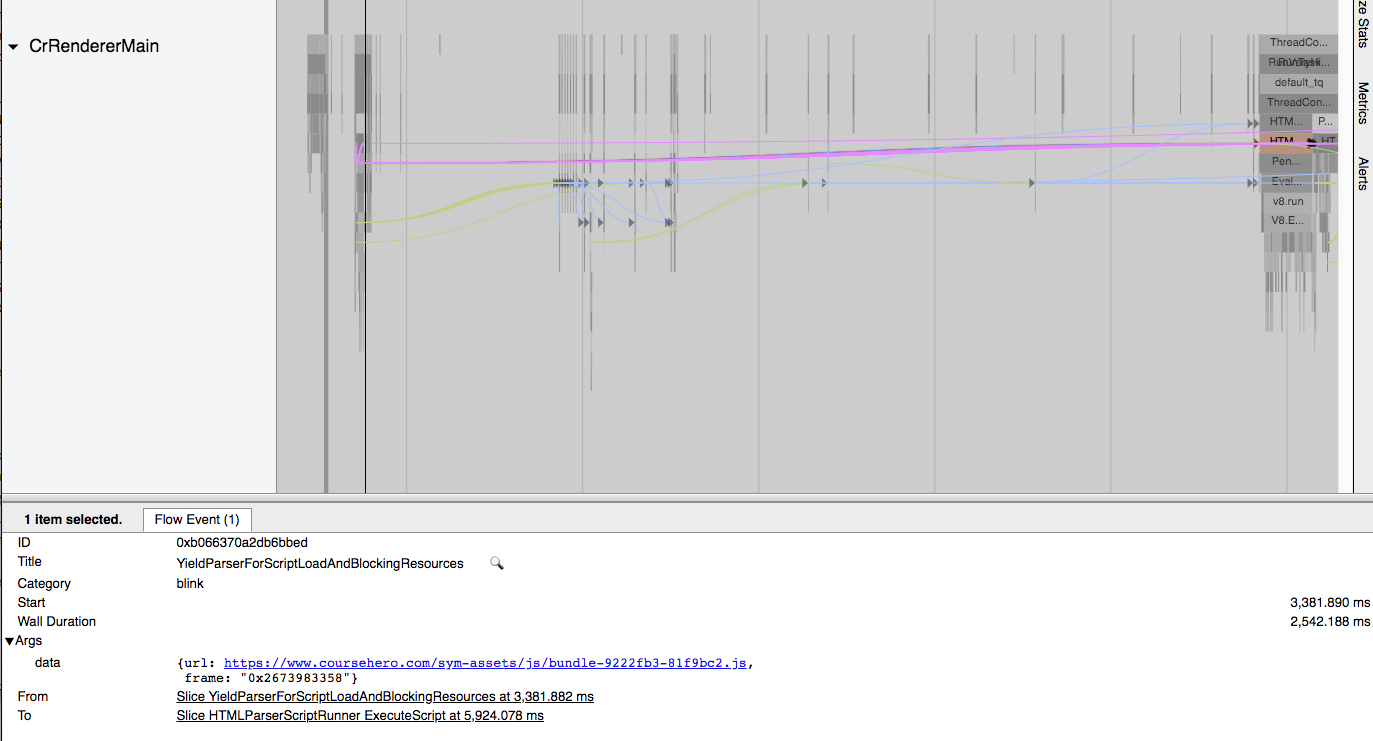
These trace events tell us exactly what blocks the rendering, and for how long. I'm not seeing an equivalent trace for render blocking stylesheets. |
|
i see these two pieces as well:
pat meenan should know more as he used to work on this. |
|
The
not seeing a way to get the blocking stylesheet from the style engine. Looks like the html parser should be doing the same with stylesheets, but doesn't yet...according to this TODO: https://cs.chromium.org/chromium/src/third_party/blink/renderer/core/script/html_parser_script_runner.cc?l=435-440&rcl=cd815ad39e59ea3a66e67206f0105b1dd298da5f We can easily get blocking information from the trace for scripts. For stylesheets, looks like some Chromium changes would be needed. But, AFAIU, it's pretty simple to determine what stylesheets block paint - any in the head, never in the body, and the duration it blocked for is how long the request took. Is that right? |
|
Anywho, how would this information be used? would the only change be replacing all of |
Just checking if we're on the same page. How do we easily determine this? :) |
|
My hunch is that https://cs.chromium.org/chromium/src/third_party/blink/renderer/core/script/html_parser_script_runner.cc?type=cs&sq=package:chromium&g=0&l=111-126 will do nicely. I haven't tried yet :) |
|
Comparing the However, the timestamp on the event suggests it blocked for a few microseconds, whereas we currently suggest it to be 40ms? Is that right? trace |
|
I'm assuming the time it's reporting (in (No clue if this is true or not, just my hunch :) |
|
Thanks @paulirish. So a The relevant flow trace event is: This comment suggests that the html parser doesn't have the same blocking mechanism for stylesheets. But, I don't think it's needed, AFAIK a stylesheet only blocks if there is a script to block for, and this case is handled in I suppose what's left is to determine what stylesheets (the resource the script is waiting on) is doing the blocking. |
|
Running against sfgate.com shows the big difference here: we'd be reporting on what the browser actually blocked on, not what it could possibly block on. Note just the one script from inspecting the traces, but many from the current artifact code. patchoutput (sfgate.com) |
|
Perhaps I'm still completely missing the boat here, but was what I was spitballing anywhere close to reality afterall? It sounds to me like the events in the trace are what was actually blocking as the load happened, i.e. we're only really getting data on the current observed bottleneck and not the full picture of what's render-blocking that we would need for simulation. |
yeah that seems right ... fixing whatever script the parser blocks on could just reveal the very next script as being blocking, without ever giving us the full picture. the parser blocks on the result of
checks for a blocked state on an
Just checks a counter, which is only incremented here. But perhaps adding hooks to these two things (there's no existing trace for these things like the one in the parser) would suffer from the same problem. |
|
Four ways a style sheet blocks the parser via the This covers stylesheets loaded via Only called from creation of inline css from XML stylesheets. Move along now. This class handles any Increments the counter for Not sure where any of these |
|
🎉 soon we'll have a trace event for render-blocking styles: https://chromium-review.googlesource.com/c/chromium/src/+/2626665 |
|
The CL still has a bunch of open questions in the form of TODOs. I'd love y'all's opinions on the answers:
/cc @paullewis @pmeenan |
|
Speaking for WebPageTest:
|
OK, thanks! I left it out for now, but may tackle it in the future.
I fixed that with https://chromium-review.googlesource.com/c/chromium/src/+/2626665/13..14
Seems like the link_style.cc call site only considers "created by parser" styles as blocking (even if they are still high priority)
Yup. Added that support in https://chromium-review.googlesource.com/c/chromium/src/+/2626665/14..15 |
|
https://chromium-review.googlesource.com/c/chromium/src/+/2626665 landed! (including redirect support) |
update 1: there were some followups, too. see https://chromium-review.googlesource.com/q/hashtag:devtools-cwv+(status:open%20OR%20status:merged) update 2: render-blocking status for scripts is now also landed! 🎉 |
|
Here's what I have so far. I'll highlight the differences between renderBlocking trace and Lighthouse's manual TagsBlockingFirstPaint on dbw_tester.html.
@yoavweiss, items 2, 3, 4 and 6 don't match my expectations here. WDYT? Every request on the page + |
my take on 'em: late in-body script (jquery.min.js aka +1):.. @yoav is the table in Chrome Resource Priorities and Scheduling still accurate? IMO calling this blocking is opinion so i'm glad the trace event gives identifies it as in-body and lets us decide :)
|
The table should largely still be accurate. Agree this is somewhere where y'all can be more opinionated :)
Agree this should not trigger a fetch at all, and definitely not a high priority/blocking one. As it stands (from casually looking at the code), I think it does, so the reporting seems correct. /cc @foolip and @mfreed7 who may have opinions on the compat implications of this.
Should not be blocking, so this sounds like a reporting bug. I'll look into it.
Haven't we deprecated those? |
https://chromium-review.googlesource.com/c/chromium/src/+/2791427 |
I also agree that
I just +1'd your CL for this.
What's a |
Currently markup based preloads are considered blocking [1]. This CL makes sure that they're considered non-blocking, along with dynamically added preloads. [1] GoogleChrome/lighthouse#2065 (comment) Change-Id: Ie11b67be1992751342f16bb3aee62b519b9582ff Bug: 1193760 Change-Id: Ie11b67be1992751342f16bb3aee62b519b9582ff Reviewed-on: https://chromium-review.googlesource.com/c/chromium/src/+/2791427 Reviewed-by: Mason Freed <masonf@chromium.org> Commit-Queue: Yoav Weiss <yoavweiss@chromium.org> Cr-Commit-Position: refs/heads/master@{#867694}
Currently markup based preloads are considered blocking [1]. This CL makes sure that they're considered non-blocking, along with dynamically added preloads. [1] GoogleChrome/lighthouse#2065 (comment) Change-Id: Ie11b67be1992751342f16bb3aee62b519b9582ff Bug: 1193760 Change-Id: Ie11b67be1992751342f16bb3aee62b519b9582ff Reviewed-on: https://chromium-review.googlesource.com/c/chromium/src/+/2791427 Reviewed-by: Mason Freed <masonf@chromium.org> Commit-Queue: Yoav Weiss <yoavweiss@chromium.org> Cr-Commit-Position: refs/heads/master@{#867694} GitOrigin-RevId: e25639bedc5e4a37374789ef46cb1fb704170842
|
https://chromium-review.googlesource.com/c/chromium/src/+/5208571 With the latest changes to Chrome, the trace's |
|
I'm using the following script to compare URLs: url=$1
node cli $1 -G --quiet --chrome-flags="--headless=new"
frame_id=$(cat latest-run/defaultPass.trace.json | jq -r '.traceEvents.[] | select(.name == "TracingStartedInBrowser") | .args.data.frames[0].frame')
old_urls=$(cat latest-run/artifacts.json | jq -r ".TagsBlockingFirstPaint.[] | .tag.url" | sort)
new_urls=$(cat latest-run/defaultPass.trace.json | jq -r ".traceEvents.[] | select(.name == \"ResourceSendRequest\" and .args.data.renderBlocking == \"blocking\" and .args.data.frame == \"$frame_id\") | .args.data.url" | sort)
sdiff <(echo "$old_urls") <(echo "$new_urls")The outputs match on most sites that I tested (https://espn.com, https://cnn.com, https://theverge.com) but I did notice that https://store.google.com differs because resources are marked as |
https://github.com/GoogleChrome/lighthouse/blob/master/lighthouse-core/gather/gatherers/dobetterweb/tags-blocking-first-paint.js#L58 only checks for
scriptin<head>.We should expand that to cover blocking scripts within
<body>(example). False positives will likely be trickier to deal with. Strawman below.For all scripts in
<body>:document.body.lastElementChild).script,template, and anything else in the default stylesheet that's hidden by default.node.offsetParent === nullto determine if it is being rendered. Note: cannot usegetComputedStyle(node).display === 'nonewon't work as expected.We'll need to also update the reference do, which talks about scripts in the head:
https://developers.google.com/web/tools/lighthouse/audits/blocking-resources
cc @igrigorik
The text was updated successfully, but these errors were encountered: